Ovo je nastavak na članak koji vam se mnogo dopao i još jedan prikaz kako bukvalno neko ko nije hacker može da nanese veliku štetu vašoj firmi. Uz ovaj članak, naučićete odakle preti opasnost i kako da se zaštitite od toga.
Pre nego što krenete dalje, ako niste pročitali obavezno pročitajte prvi deo ove priče – hakovanje fejsa i instagrama uz ispijanje kafe!
Članak je priča sa terena našeg prijatelja Vlade, on će vam preneti svoje utiske, a mi ćemo malo analizirati, šta je problem i koje je rešenje!
Korišćenje javnih mreža u poslovne svrhe zna da bude mnogo opasno iz tog razloga što zlonamerni napadač može doći do krucijalnih stvari koje mogu oštetiti vašu firmu.
Citat:
Aplikacija koju sam koristio u ovom slučaju se zove ` Intercepter-NG `.
Začudio sam se čto ima da se skine regularno na android marketu!
Da bi aplikacija radila, potrebno je da Android bude rutovan i da se ima instaliran skup Unix alata poznatih kao ` busybox`.
Aplikacije je sniffer koja može da presreće sledece protokole : ICQ\IRC\AIM\FTP\IMAP\POP3\SMTP\LDAP\BNC\SOCKS\HTTP\WWW\NNTP\CVS\TELNET\MRA\DC++\VNC\MYSQL\ORACLE\NTLM.
Primer koji sam uradio je presretanje poslovnog saobracaja jedne firme, gde sam došao do informacija o username-u i password-u njihovog e-maila.
Demonstracija hakovanja e-mail-a
Slika početka presretanja >
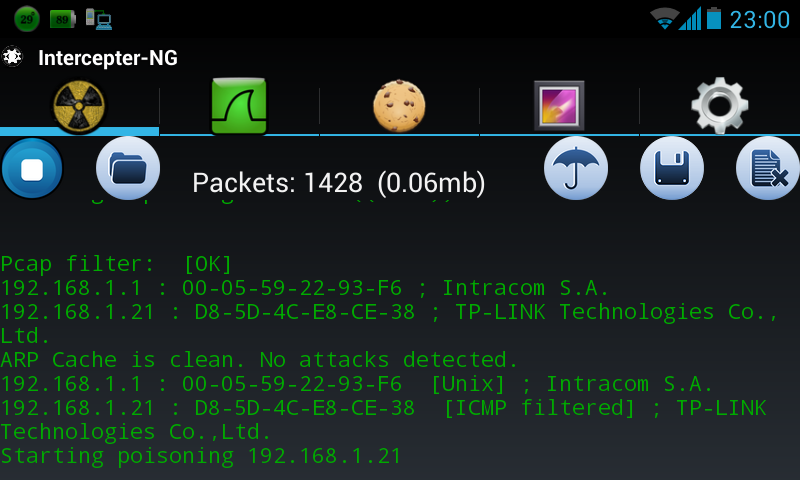
Slika nadgledanja saobraćaja >
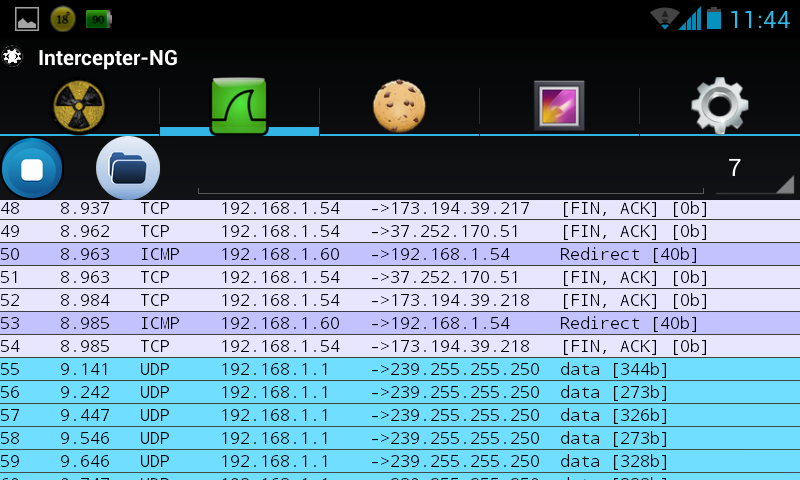
Pojavljivanje šifre u saobraćaju >
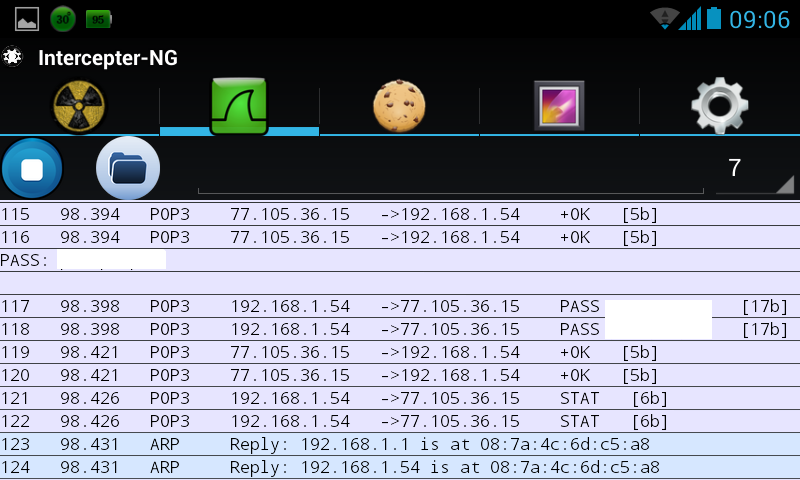
Pronalaženje username-a i passworda >
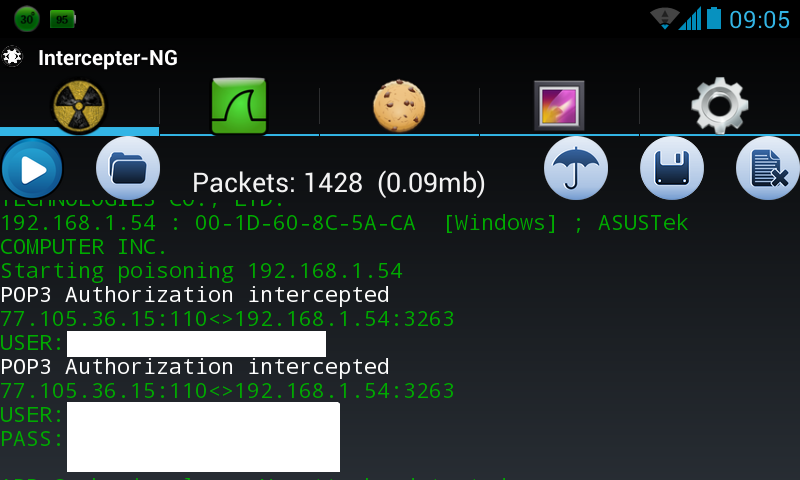
Šteta može biti ogromna, zato što uvidom u poslovnu komunikaciju firme, napadač može doći do mnogo bitnih informacija i naneti veliku štetu!
Šta se vidi na slikama i kako je ukraden password?!
Poslednja slika prikazuje rezultat snimanja mrežnog saobraćaja na javnoj wireless mreži. Gde se pojavljuje username i password u čitljivom obliku!
Šta je javna wireless mreža?!
Pa ništa drugo, nego otvorena wireless mreža u kafiću, školi, bolnici… Gde su svi korisnici zakačeni na isti Access Point i gde su svi u istoj mreži. Ako je mreža zaštićena passwordom, to ne znači da ste zaštićeni od ovakvog napada.
Šta je napadač dobio?
Ukradeni su kredencijali (username i password) za pristup korporativnom e-mail nalogu. Pomoću tih podataka u mogućnosti ste da se ulogujete kao oštećeni i čitate poverljive informacije koje se šalju e-mail porukama. Ne samo da možete da čitate, već možete da šaljete poruke i tako sakrijete svoj identitet.
Šta je oštećeni radio?
Sa slika se uz pomoć mrežnih alata može vidieti da je u pitanu plesk05.orion.rs [77.105.36.15] i protokol POP3 (protokol za prijem mailova)
Plesk predstavlja web/mail server za .aspx stranice – U pitanju je Windows hosting server Orion Telekom-a.
Username je namerno izbrisan sa slike da ne bi bilo zloupotreba, a on je obicno u obliku [email protected].
Žrtva ovog napada se zakačila na otvoreni wireless i samo je pokrenula neki e-mail client (Outlook Express…), kako bi proverila poštu. Korišćeni e-mail klijent je podešen tako da se da se autentikacija vrši pomoću clear text passworda.
Kako se zaštiti od ovih napada?
Sve ovo je napisano samo iz jednog razloga! Želimo da probudimo svest naših čitalaca o tome kako mala nepažnja može imati velike posledice. Nikada ne znate ko je sve od korisnika povezan na istu mrežu, nemate pojma šta sve izlažete riziku. Prevencija i edukacija je najbolja zaštita.
- Izbegavajte korišćenje javnih wireless mreža, posebno u poslovne svrhe – možda neko snima saobraćaj! Napomena, ako je wifi zašticen WPA passwordom, to ne znači da ste zaštićeni, ukoliko je i napadač već zakačen na taj wireless.
- Ne logujte se na stranice koje nisu HTTPS. Pri autentikaciji, kod obicnih stranica HTTP, salje se clear text i snimanjem mrežnog saobraćaja je moguće dobiti čitljive podatke. Na pr: Facebook, Google su HTTPS i delom su zaštićeni, ali moguće je i probiti njih, ali to ne može baš svaki klinac sa Android aplikacijom.
- U okviru e-mail klijenta ne koristiti clear text autentikaciju. Ovo zavisi i od podešavanja samog servera, tako da ako je admin u firmi tako podesio server, krađa podataka je delom i njegova zasluga.
- U okviru Access Point uređaja, uključiti AP Isolation ili Client isolation.
- Na PC-u isključiti File Sharing.
- Po mogućstvu, koristiti VPN saobraćaj koji je kripotovan, mada, pri uspostavljanju konekcije, moguće je ukrasti „kredencijale“.
- Obavezna upotreba Antivirus i Firewall-a.
- Čitajte ovaj blog i saznajte na koje načine možete biti hakovani, samim tim znate kad preuzimate rizik! Ne tražimo ništa za uzvrat, eventualno Like ili Share, ako ste naučili nešto novo i korisno. Lep primer su kolege iz Eunet-a.
Pazite cemu pristupate kada ste na javnoj wireless mrezi https://t.co/RVJmdDE0G4
— EUnet Hosting (@EUnetHosting) October 31, 2013
Napomena
Sve što je napisano u ovom članku je isključivo u edukativne svrhe. Podsetićemo vas koji je naš moto.
Cilj nam je da sve, što se u Srbiji na žalost još uvek debelo naplaćuje od strane raznih majstora, približimo prosečnoj osobi sa ovih prostora na jednostavan, razumljiv i prihvatljiv način. Ne tražimo ništa za uzvrat. Dovoljno je da se ponovo vratite na ovu adresu, naučite kako da sami sebi rešite problem i sigurnije zagazite u IT svet.
 Umrežen Blog Blog o umrežavanju i internetu. Tutorijali, SpeedTest, Merenje Brzine interneta, Telekom ADSL, Telenor, VIP, Sbb, Orion.
Umrežen Blog Blog o umrežavanju i internetu. Tutorijali, SpeedTest, Merenje Brzine interneta, Telekom ADSL, Telenor, VIP, Sbb, Orion.